SnykCon 2021 recap #2: Supply chain security, the future of cybersecurity, automation as an enabler, and more
October 8, 2021
0 mins readWhat a week! Rather, what a three days! I still can’t believe how much developer security goodness we were able to pack into SnykCon 2021. From the expert talks to the insightful discussions to the interactive workshops, I think we really delivered on our theme of helping people learn how to Build Securely.
If you attended SnykCon, thank you! We hope you enjoyed yourselves and found the content as helpful and actionable as we hoped you would. If you couldn’t attend, we already have the talks up on our SnykCon page for you to watch at your convenience.
Just like yesterday, let’s take a look back at the day’s events!
Snyk Impact partners: Career Village and The AI Education Project
Yesterday, we announced the launch of Snyk Impact during the SnykCon keynote. Today, Dipti Salopek (Snyk Chief of Staff) dug deeper into how Snyk is giving back and how we’re working with Fast Forward to make sure we can maximize our impact. After that, she handed the mic off to two inspiring leaders that are Fast Forward alumni: Jared Chung, Founder and Executive Director of Career Village and Ora Tanner, Co-Founder and Chief Learning Officer of The AI Education Foundation.
Career Village is a non-profit that crowdsources career mentorship for underrepresented youth. It’s an amazing platform that lets volunteer mentors provide guidance to young people who may not know who to reach out to for help with questions they have about career development. “[Career Village] is often the first time our students have had a serious conversation with an adult about careers, which makes it a really life changing experience for them, because when you answer their question, you’re validating them. You’re showing them that there’s somebody who believes in them, who takes their goals seriously. And that is incredibly empowering for a young person,” said Chung.
The AI Education Foundation (AIEDU) is a non-profit created to “educate students — especially those disproportionately impacted by AI and automation — with the conceptual knowledge and skills they need to thrive as future workers, creators, consumers, and citizens.” AI is going to drive job market transformation, and AIEDU makes sure that young people impacted by these shifts have the opportunity and access to learning to keep them ahead of the curve. “We built a digital curriculum to introduce students to the knowledge and skills that will be necessary to thrive in a society where AI and automation are increasingly being a part of every industry,” said Tanner.
So many (more) sessions
Understanding Supply Chain Security for Developers
With high-profile supply chain attacks often appearing in the news recently, the first talk of the day was timely. Justin Cormack, CTO of Docker, discussed the software supply chain and its growing relevance in a cloud native environment. He also explained the security risks and some ways to stay secure.
While the software supply chain is a key part of cloud native applications, it’s also becoming the most vulnerable part of modern software. Since vulnerabilities in dependencies are one of the main supply chain risk areas, Cormack believes open source library security should be everyone’s responsibility, not just the primary project maintainers. “The path from your code to production is vulnerable to all sorts of security issues,” said Cormack. “If you’re a hacker, rather than attacking some code in production, it’s often easier to do it earlier.”
The Future of Cyber Security from a Friendly Hacker’s Perspective
Keren Elazari, a security analyst who refers to herself as a friendly hacker, spoke about what cybersecurity might look like in the near future. During the talk, she discusses some of the major hacks and hacking technologies from the past 18 months, including Ryuk ransomware, Jxplorer supply chain attacks, and the SolarWinds attack.
According to Elazari, we need more hacker heroes as part of a “digital immune system” that keeps the world safe. In addition, Elazari believes the shift to working from home has transformed remote employees into the first line of defense against cyber threats. “For a lot of people, the everyday security decisions that they make actually have a security impact for the entire organization,” said Elazari. “It’s very popular to refer to people on the other side as the weakest link in the security chain, but I think we need to talk about them as the first line of defense.”
Building an AppSec Program from the Ground Up
Next up was a panel about the challenges with building an AppSec program from scratch. The panel was hosted by Lindsey Serrafin, VP of Customer Success at Snyk, included Gagan Bhatia, Head of Cybersecurity Deliver at 10x Banking, Nicholas Vinson,Head of DecSecOps at Pearson, and Stephan Steglich, Application Security Product Manager at Sky Betting & Gaming.
According to Vinson, security was very siloed in the past, where there was little collaboration between security, risk, and development teams. “We tried to partner with those teams to get developer-first requirements and get solutions that fit in with our tech stack and engineering practices. We also worked with the teams to introduce security as a normal development activity.”
Bhatia agreed that breaking down silos is a classic problem in the industry. He believes the key to breaking these silos down is finding the right tools for developers and focusing on the developer experience. “We talk about the customer experience, but there’s another angle that we need to always think about. How do you give developers the tools or guidance to do their job?”
Finally, Steglich discussed the importance of incremental continuous improvement. “Using metrics you can say anything that meets your own goals if you spin them correctly. So think carefully about the metrics you put out there.”
Security is like starting to cook. You’re not going to make a world-class dish the first time, but you should just start cooking.

Stephan Steglich
Application Security Product Manager, Sky Betting & Gaming
What the H... is This Signing Thing About ?
Rachid Zarouali, Cloud Architect at sevensphere discussed the importance of signing and scanning Docker images for comprehensive container security. Image signing is a mechanism for verifying the integrity of images and ensuring they weren't tampered with.
While image signing is crucial, Zarouali also discussed how it’s much more powerful when combined with vulnerability scanning. That’s because signed images can still include vulnerabilities that introduce security risks. “Image signing can help improve the security of your images, protecting from tampering, man-in-the-middle, and replay attacks,” said Zarouali. “As you saw in this brief demo, signature and validation mechanisms are also fairly easy to implement.”
Hacking Your Infra From the Outside by Exploiting npm Dependency Confusion Attacks
Liran Tal, Director of Developer Advocacy at Snyk, demonstrated how you don't need to use the force to take down the Death Star — all you need is dependency confusion. Tal walked through how dependency confusion works, why it's so effective, and how you can stay safe from it. It was an amazing talk that gave actionable tips for mitigating dependency confusion attacks and defending your software from falling to the dark side!
Automating open source license approvals
While most developers know about open source, they don’t realize the licensing compliance issues that often go along with using the code. Sam Hodgkinson and Ben Davies, both software engineers at Citrix, described how they were able to reduce open source license approvals from two weeks to seconds using Snyk. Implementing Snyk Open Source license compliance solved the need for an automated process that operated within the company’s legal framework to quickly approve open source requests during development.
In order to streamline the management of open source licenses for over 10,000 code projects, Citrix built a policy API that aligns with the company’s legal requirements. This policy API provides automated approval decisions based on Snyk open source license data during the CI/CD process. “By using Snyk and finally driving through some of the technical barriers, we’ve been able to fully automate this process,” explained Davies. “We’ve taken a two week process and reduced most policy decisions to seconds.”
Evangelizing the SRE mindset: Building a culture of reliability and ownership
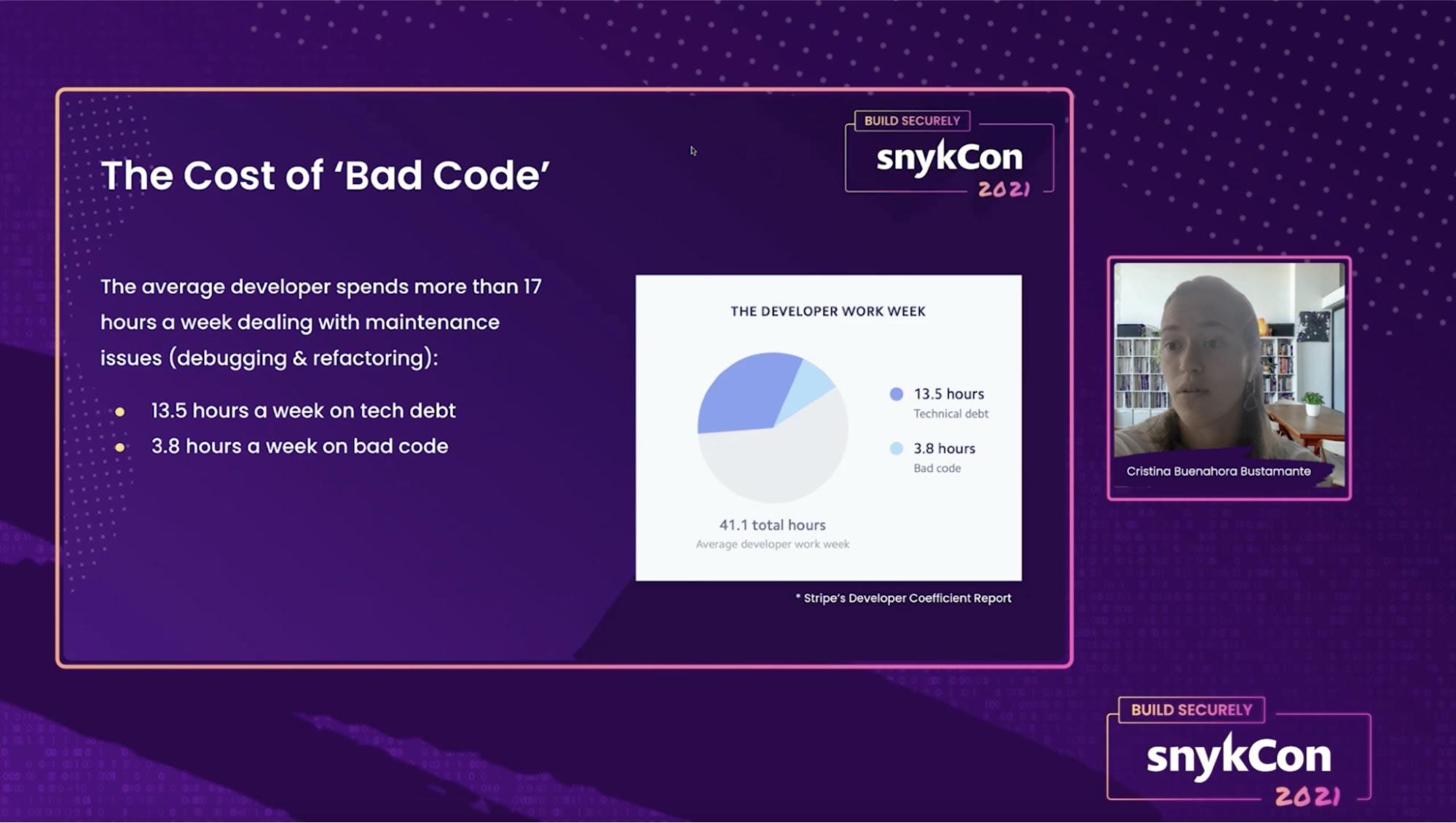
In her session, Cristina Bustamante, Founding Engineer at Cortex spoke about the role of site reliability engineers (SREs) and how minimizing bad code is a benefit for everyone, including development and security teams.
When there are bugs or security vulnerabilities within a piece of code, this introduces technical debt that can impact the reliability and security of an application. By focusing on an SRE mindset, however, development teams can ship cleaner code that improves an application’s resilience long term. “An estimated 85 billion dollars a year is spent on developers dealing with bad code,” stated Bustamante. “That’s a lot of time and money that could be going toward developing new features for your clients.”
Workshops, product talks, and demos
If you read yesterday’s blog, I know that you’ve likely been waiting all day for this section. So here it is… the list of amazing demos we ran over the past two days:
How to successfully Roll Out Snyk across your Business/Enterprise
So you bought a Team Plan, what now?
How do you know what to fix when you can't fix it all?
Snyk + AWS, Better together
Using Snyk Effectively with Github
Using Snyk Effectively with Gitlab
Becoming secure Javascript / Node developer
Becoming a secure Python developer
Becoming a secure Java developer
Becoming a secure Go developer
Introducing the .snyk file - Defining policy at the desktop/CI level
CI/CD Best practices & Advanced Tips
Staying Compliant - Leverage Snyk license management features while you develop
Secure Containers Easily with Base Image Management
Securing your Terraform Deployments
Pod Problems: Securing a Vulnerable Kubernetes Application with Snyk
Creating custom rules for Snyk Infrastructure as Code
Securing your code using Snyk Code in 15 minutes
Totally worth the wait, I know. Aside from those great product demos, we also had great product talks about container security, ML-powered code analysis, securing open source dependencies (wisely), and more. And of course, two more hands-on workshops: Never Get Pwned! Understanding the OWASP Top 10, hosted by Grant Ongers (CTO at Secure Delivery, Global Board of Directors at OWASP Foundation) and Kubernetes IaC Security Gamified, hosted by Kim Schlesinger (Developer Advocate at Digital Ocean).
Fun fact: Schlesinger was the only non-Snyker to have multiple sessions, as she also ran the 3 Things You (Probably) Don’t Know About SSH lightning talk. Great job, Kim!
Thanks for tuning in to SnykCon 2021
Well, that’s a wrap for SnykCon 2021! The industry experts delivered some exciting and inspiring talks that continue to push forward our understanding of application security. We hope you had the opportunity to gain new insights that you can apply to your own projects. And if there were any talks you missed — or wanted to watch again — watch them on-demand on the SnykCon page.
Build Securely!





















